The Police State, Cyber Operations and Loss of Freedom on the Net
![]()
![]()
![]()
![]()
![]() DO NOT TRUST TOR (Guard is an IP/MAC Identifier)
DO NOT TRUST TOR (Guard is an IP/MAC Identifier)
![]()
![]()
![]()
![]()
![]()
![]()
![]() Realtime Cyber
Warfare Attack Intelligence
Realtime Cyber
Warfare Attack Intelligence
The West Only Knows How to LIE LIE LIE LIE LIE LIE LIE LIE LIE
FBI, DHS, and UK cyber agency warn of Russia internet attack that targets routers
![]()
![]()
![]() Courses Pirated &
Dumped by Case, S1rlancelot & dave + Random
Courses Pirated &
Dumped by Case, S1rlancelot & dave + Random
https://ghostbin.com/paste/8hcw8
https://github.com/toddmotto/public-apis
http://www.mediafire.com/file/qchaazzxrdsmwja/CloudFlare+Security.rar
![]()
![]()
![]() 07.01.2019 W i n d o w s 2 0 0 0 Source Code
07.01.2019 W i n d o w s 2 0 0 0 Source Code
http://www.jar2.biz/Files/windows_2000_source_code.zip
![]()
![]()
![]()

October 17, 2017 - Operating Servers and JAR2 com in Russia for the last 14 years has been a challenge and sometimes it has been all out warfare so I would like to share some of my knowledge and give you some of the main points I use in this environment to secure yourself against military and government grade hacker attacks, CIA/NSA malware/spyware installs and the like.
1. Passwords and Accounts
a) Due to weaknesses still in existence in encryption and decryption programs passwords over 27 characters can not be cracked. The threshold for determining password length even for the NSA is 25/27. After 27 it is impossible for them to determine if your password is 28 or 52 or even 102 therefore without knowing the password length there is no way to crack it. DO NOT USE words, names or even formulas in passwords. Use a random series of upper and lowercase letters, numbers and symbols and do not use the same password for different machine accounts. Do not use your machine account passwords for websites or even your phone. One way to recall and generate a random password is to use a figure on your keyboard although eventfully any random series will be learned by rote. Do not save your passwords in a file on your computer and do not keep them where someone may get access to them. Even your better half. On the web use different passwords for all site and services. This can be difficult with the number of passwords people need to use today but a simple method of at least choosing for example, a prefix or suffix on a memorized random series of over 27 character will help you. Some sites will not let you make a password of over 27 characters. This is why and these sites you should never trust with your sensitive data.
b) For Windows: Never use the root Admin account to do anything except when installing your new operating system and drivers. After your fresh install always create a Power User account and always use it to install programs and serf the net. You can go hyper paranoid and go down to a user or guest level account but that will limit funtionality and cancels out the next point. Disable the guest account on the computer. Disable all of the Microsoft accounts and remote service accounts. On my work computer I have only two active accounts and the two associated groups. The renamed default Admin Account and the Power User account and everything works fine. XP and Windows 7 have attempted to obfuscate these basic security parameters by installing multiple services that do the same things. For example they introduced the Security Polices plug-in and the local users and accounts and then the Security Center which in certain cases cancel each other out or make any changes in one uselss, maintaining the backdoors for Microsoft. Then there are dozens of built in registry key and switches that you will have to change to completely secure yor system. That is what it is all about. Micorsoft Windows is the greatest spy tool every developed in the world. Within its hidden code are dozens of backdoors as we have even found out is true for INTEL hardware.
2. Installing and Updating secure and locked down Windows Systems: Is it possible to secure Windows?
a) The highest Windows you will be able to safely keep running in Russia would be Windows 7 Ultimate service pack 1 and you will never be able to safely update. Why? Microsoft is running under the anti-Russian US Sanctions regime. MS has updates that will blue screen and kill your system and make it unsavable requiring a complete fresh install. This includes a documented video driver upgrade that blue screens your machine and deletes all restore points.
b) Installing - If you had 7 you will have to delete and format the original root partition. It hides programs and code that allow for root level access to your machine using built in MS user accounts (when up and running delete or disable all such accounts) and BIOS connectivty though the INTEL installed spy chip accesible through BIOS or other methods detailed above. BEFORE you install Windows 7 make sure you have all of your drivers on seperate media. Air gap your system and disconnect all possible wireless access while you Install 7, this includes your Wi-Fi and all wireless devices that you may connect to. This includes wireless keyboards, mice, printers and everything and anything else else that would allow for access to your machine. Of course a virtual machine would also give you an added layer. MS7 run in a LINUZ box under a virtual machine is probably the safest way to install 7 but this is extremely time consuming and a real pain in the ass to run under.
c) Configuring (THIS WAS STOPPED BECAUSE I CAN NOT GIVE AWAY MY CONFIGURATION)
d) Updating
3. Browsing, Browsers and the WWW
4. Sub-Level Protection and Military Grade Government Hacks and Atacks
5. Programs, VPNS, Malware and Downloads
6. Processes
7. Permissions and Access
8. Ports
9. E-Mail, Phishing and Government Grade Malware Exploits
10. Device Access: Cameras, Microphones, USB and Keyboard Sniffers
11. Social Media and "Secure" Apps and Communications

![]()
![]()
![]() CARNIVORE/ECHELON/PRISM/Boundless
Informant/Etc KEYWORDS
CARNIVORE/ECHELON/PRISM/Boundless
Informant/Etc KEYWORDS
http://jar2.com/2/NSA/NSA_KEYWORDS.html
![]()
![]()
![]() US Military and CIA Cyber
Operations Surrogate in Ukraine Targetting JAR2 and More
US Military and CIA Cyber
Operations Surrogate in Ukraine Targetting JAR2 and More
http://www.jar2.com/Topics/Ukraine_ATO_SBU_Leak.html
![]()
![]()
![]() Euro Working Group on Non-Lethal
Weapons and Covert Harassment
Euro Working Group on Non-Lethal
Weapons and Covert Harassment
European Working Group Non-Lethal Weapons (EWG-NLW)
![]()
![]()
![]() COVERT HARASSMENT CONFERENCE
2014 - Includes Cyber Operations
COVERT HARASSMENT CONFERENCE
2014 - Includes Cyber Operations
COVERT HARASSMENT CONFERENCE 2014, BRUSSELS, 20 NOVEMBER 2014
![]()
![]()
![]() Reading Privileged Mem CIA/NSA
Exploit
Reading Privileged Mem CIA/NSA
Exploit
Reading Privileged Memory With a Side-Channel
![]()
![]()
![]() US Army Concept Cyber and Electronic Warfare
Operations
US Army Concept Cyber and Electronic Warfare
Operations
http://www.jar2.com/INDEX.html
The U.S. Army Concept for Cyberspace and Electronic Warfare Operations January 2018
![]()
![]()
![]() 13 Russian Hackers Installed Trump?! Okay Let's
Look for Proof
13 Russian Hackers Installed Trump?! Okay Let's
Look for Proof
http://www.jar2.com/Files/NWO/cyber-hijack-findings.pdf
Files/USGOV/internet_research_agency_indictment.pdf
Files/USGOV/Elections/TFESReport.pdf
http://www.jar2.com/Files/Downloads/JAR_16-20296A_GRIZZLY%20STEPPE-2016-1229.pdf
![]()
![]()
![]() DOJ Cyber Crime Find My
I-Phone Spy Pre-Installed Apple/NSA Spyware
DOJ Cyber Crime Find My
I-Phone Spy Pre-Installed Apple/NSA Spyware
![]()
Forensic Investigation of Clandestine Laboratories (Study 373 pages)
![]()
![]()
![]() Computer Networks and Information
Warfare Implication for Military Operations
Computer Networks and Information
Warfare Implication for Military Operations
http://www.jar2.com/Files/USGOV/csat17.pdf
![]()
![]()
![]()
![]() These Progams With a Little
Tweeking Will Help Block Almost All Intrusions
These Progams With a Little
Tweeking Will Help Block Almost All Intrusions
ftp://www.jar2.com/Securing%20Your%20Systems/
![]()
![]()
![]()
![]() Microsoft Hosts File Blocklist:
A Must for Win Comps and Routers
Microsoft Hosts File Blocklist:
A Must for Win Comps and Routers
C:/Windows/System32/drivers/etc
http://www.jar2.com/Files/MShosts.txt
http://www.dslreports.com/forum/r30676597-Complete-Win10-blocking-host-file
![]()
![]()
![]() Stop "MailRu" 90% of Current
Malware - Absolutely Necessary on Mozzila
Stop "MailRu" 90% of Current
Malware - Absolutely Necessary on Mozzila
http://www.ghacks.net/2013/02/20/how-to-block-new-add-on-or-plugin-installations-in-firefox/
![]()
![]()
![]() NSA Windows XP Security Guide:
Still a Good Guide for Securing Clean Install
NSA Windows XP Security Guide:
Still a Good Guide for Securing Clean Install
http://jar2.com/3/4/Downloads/wxp-securityguides.zip
![]()
![]()
![]() Secure Communications Operational Tradecraft
(2002 - Still Topical)
Secure Communications Operational Tradecraft
(2002 - Still Topical)
www.jar2.com/Files/Secure_Communication_2002.PDF
![]()
![]()
![]() Secure Communications Operational Tradecraft
(1999 - Still Topical)
Secure Communications Operational Tradecraft
(1999 - Still Topical)
Files/Secure_Communications_1999.pdf
![]()
![]()
![]() Pisces: Anonymous Communications
Over Social Networks
Pisces: Anonymous Communications
Over Social Networks
http://www.jar2.biz/Files/GUCCIFER_AND_ANON_HACKS/anonymous-sm-comms.pdf
![]()
![]()
![]() Hacking Firewalls and Networks
Hacking Firewalls and Networks
![]()
![]()
![]() The Hacker's Handbook By Hugo Cornwall
The Hacker's Handbook By Hugo Cornwall
http://www.jar2.com/2/Computing/Hugo%20Cornwall%20The%20Hacker's%20Handbook.htm
![]()
![]()
![]() Hacking Firewalls and Networks: How to Hack
into Remote Computers (356 pages)
Hacking Firewalls and Networks: How to Hack
into Remote Computers (356 pages)
![]()
![]()
![]() Pentester Lab Web Penetration Testing (106 pages)
Pentester Lab Web Penetration Testing (106 pages)
http://www.jar2.com/Files/Books/web_for_pentester.pdf
![]()
![]()
![]() Hacking for Dummies: Test Network Security Ethically
(387 pages)
Hacking for Dummies: Test Network Security Ethically
(387 pages)
http://www.jar2.com/Files/Books/Hacking_for_Dummies.pdf
![]()
![]()
![]() The Art of Intrusion: Hacker, Intruder and Deceiver
Exploits (291 pages)
The Art of Intrusion: Hacker, Intruder and Deceiver
Exploits (291 pages)
www.jar2.com/Files/Leaks/Hudburgh/taoi.pdf
![]()
![]()
![]() GCHQ Uncensored by Richard Aldrich - 665 Pages
GCHQ Uncensored by Richard Aldrich - 665 Pages
Files/Books/GCHQ_Uncesnored_Richard_Aldrich.pdf
![]()
![]()
![]() THE NSA TOOLS FILES EQGRP MASTER RELEASED (VALUE
$500 MILLION)
THE NSA TOOLS FILES EQGRP MASTER RELEASED (VALUE
$500 MILLION)
THE NSA EQUATION GROUP FILES - NSA HACK TOOLS UNENCRYPTED
![]()
![]()
![]() The Diebold Hack: Diebold Memos and Internal
Docs Forbidden and Deleted in US
The Diebold Hack: Diebold Memos and Internal
Docs Forbidden and Deleted in US
![]()
![]()
![]() Securing Your Privacy in a Post PRISM World,
Back to Basics
Securing Your Privacy in a Post PRISM World,
Back to Basics
http://www.jar2.com/Topics/PRISM.html
![]()
![]()
![]() PRISM and Securing Your Systems from It
PRISM and Securing Your Systems from It
http://www.jar2.com/Topics/PRISM.html
![]()
![]()
![]() Secret IBM Person Tracking Patent
Secret IBM Person Tracking Patent
http://www.jar2.com/Files/USGOV/IBM_Person_Tracking_Patent.pdf
![]()
![]()
![]() Yahoo Messenger Spy
Yahoo Messenger Spy
![]()
![]()
![]() Skype Spy
Skype Spy
Skype_International_Guidelines_For_Law_Enforcement_Agencies.pdf
![]()
![]()
![]() Wireless Router Spy
Wireless Router Spy
Wireless_Router_Interrogation_PPT.pdf
![]()
![]()
![]() Explorer Spy
Explorer Spy
Shellbags_Explorer_and_Registry_Explorer_Links_Manuals.pdf
![]()
![]()
![]() Mobile Device Spy
Mobile Device Spy
Processs_Of_Mobile_Device_Forensics_PPT.pdf
![]()
![]()
![]() BitTorrent/Torrent Spy
BitTorrent/Torrent Spy
Files/FACEBOOK/Bittorrent_Case_Study.pdf
Torrential_Downpour_BitTorrent_Update_Refresher.pdf
![]()
![]()
![]() Cell Phone Spy
Cell Phone Spy
Cell_Phone_Searches_for_Law_Enforcement_PPT.pdf
![]()
![]()
![]() CraigList Spy
CraigList Spy
Craigslist_Investigations_PPT.pdf
Craigslist_Investigations_Update_P1.pdf
Craigslist_Investigations_Update_P2.pdf
![]()
![]()
![]() Google Server Spies
Google Server Spies
![]()
![]()
![]()
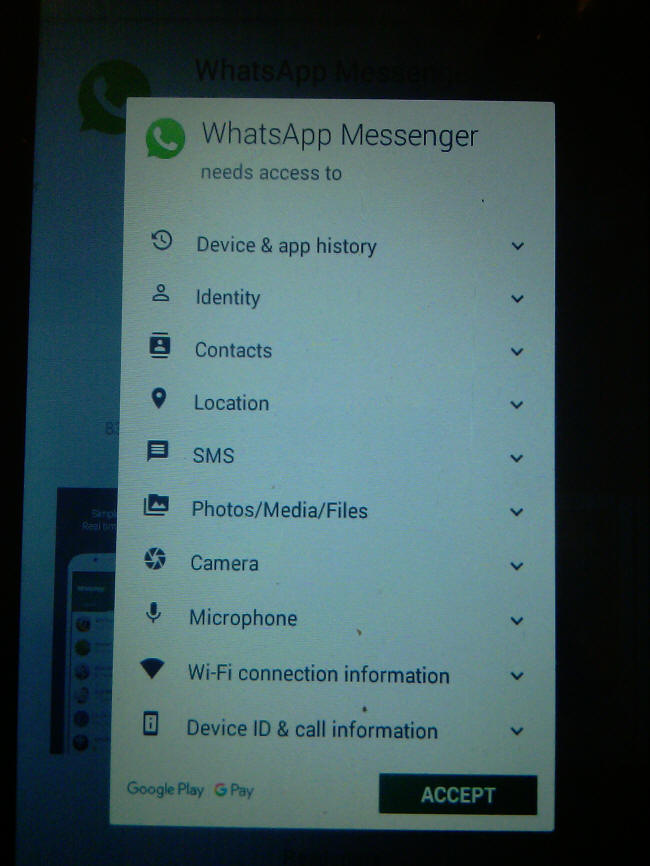
![]() 11-07-2023 The Evil of WhatsApp Continued
11-07-2023 The Evil of WhatsApp Continued
Like all smart phones, the I-Phone in particular, WhatsApp and all those little programs you use which are so convenient are Spy tools built by huge Western corporations for the Spooks of the Empire of Lies and GENOCIDE/Murder Incorporated. Today let’s focus a little on the WhatsApp monster since it is currently one the biggest sources of spy information being extracted from Russia by CIA/MOSSAD enabler Zuckerberg (House of Rockefeller). Since few of the sheeple care that everything they say and do on their phones in and out of the APP is sent to the Empire of Lies, including their locations and video and audio that can be recorded even when the APP is off, perhaps they will care if WhatsApp is clandestinely forcing them into the Satanic business model money suck of perpetual upgrades that Google and the “Tech Giants” are all involved in.
If you are “Old School” like me you remember ICQ, Skype when it was peer-to-peer and the wonderful world of SMS messaging, and if you needed confidentiality there was peer-to-peer PGP uncrackable encryption. If you are old school you remember that the NSA can not break passwords of more than 25 characters and other such wonderful things which allowed us to be Anonymous. SMSing was great for cell providers and was more than adequate for normal people and it kept the information within your providers domain, but the “Tech Giants” (CIA INQTEL et al) decided they wanted to know what you were writing about, they wanted to know your location, where you work, what you watch, how much money have, your bank account numbers, who you sleep with, etc. et al. Not only did they want everything but they wanted it everywhere. So they raped SKYPE, killed ICQ, made SMSing archaic and offered you the “chance” to communicate on their flashy Satanic messengers where all your messages, location, et al, were travelling through their servers (in the Utah dessert or wherever their Satanic Data Centers may be) every time you communicated with your interlocutor several miles away. Of course people have become sheep and even Trojan Horse Limited Hangouts never even pretend to go against the “Tech Giants” in any real way other than endless self-serving PR to maintain their legends, so “Let them have my data I have nothing to hide” has become the mantra of the sheeple. Yes you suck!
So what if I told you that all of these endless upgrades are not necessary. The corporations and the ASTEROIDS and all the rest would hunt me down and kill me, they are after all “ALL POWERFUL”! Never mind that they are the parasitic Satanic scum of the Earth forcing mankind into devolutionary self-annihilation and all deserve to be liquidated themselves but that is another story.
What if I told you that in reality your old Nokia button phone is enough for what phones are supposed to be for?
You would scream: “Heresy! Dinosaur! I need my ‘Black Mirror!!!’”
“Why?”
“Because!!!”
“Why?”
“Go to hell and die!”
In a nutshell that is the state of the truth movement and the world today. The blind have taken over and those who see must die. However this is not a treatise on the current deplorable condition of the Angelic creations that are humans, I wanted to point out how MEGA Corporation META forces the poor working, struggling, no-hope-in-sight-for-a-bright-future, citizens of the world into their parasitic Satanic unsustainable endlessly rising profit margin capital sucking upgrade trap and give you a simple solution to at least avoid one of them.
Retro “Old School” 010101 Hackers like me (LULZ) who still code and refuse to leave the “LEGACY” domain where we freely engage in time travel (just kidding) are no longer needed in the “BIG TECH” world and are demonized and silenced into oblivion by the Corporations and the Empire of Lies, but hopefully this little fix will help you as I engage in what the Internet is supposed to be for “SHARING” nice things. Anyway before this becomes an expose let me get to the matter at hand:
What’s Up with WhatsApp
Endless upgrades and the bricking of your APP. Did I say ‘your’? Yes I did. So here is the little trick that took me several hours to work out as the EMPIRE OF GOOGLE LIES has stopped listing real practical information for the common people. It all started out simple enough, I have an old Android 4 KitKat device in which I used WhatsApp for a few months in 2019 to communicate with my students and I needed to find an old contact that I worked with on a project. So I booted the device, which I maintain in a charged state, and with the hairs standing on the back of my neck, tapped the WhatsApp icon. I expected a problem due to the fact that I had a new Sim Card in the device, but that was not even an issue, the APP is attached to the MAC. What came up, and apparently this is a big issue on the Internet judging by the amount of “fake fixes”, was a screen that said the time and date on my device was incorrect with the only option to continue being a button to adjust the time and date. I tried that, did a search on the issue, tried everything including re-booting, re-installing (an old APK which would work on Android 4) and nothing. The same thing. Hacking into the database file and manually reinstalling on another device did not work either. Downloading programs to transfer data also did not work (for which you can pay 30 dollars or more). The LIARS at META who programmed their little bricking code should have written “Your program and device are outdated and we want you to upgrade, turn your clock back to a period before June 2019 to access your messages!” because that was the real issue. You see WhatsApp bricks itself when it gets “TOO OLD” perpetuating the forever parasitic Satanic upgrade profiteering for META, GOOGLE et al and allowing for the NSA/CIA spy tools to continue to be developed and deployed endlessly. So basically if you have this issue you turn your clock back, starting with the years until it unlocks. During the process I had to go through six different years and each time there were different messages, in 2020 the message was that “support for this version ended on June something 2019. So I changed the date to April 2019 and the Satanic APP opened up and demanded I make a cloud backup to SATANIC GOOGLE which of course was not possible because I could not login to GOOGLE due to the date on my device. So after several attempts I made a local back up and was allowed to finally read my messages again. Note if during the process you correct your date to access GOOGLE WhatsApp will brick again, so the only option is a local back up. I could have dug deeper but I was already fed up. My advice if you have this problem is to access your messages and delete WhatsApp and NEVER USE IT AGAIN! Telegram does not do this type of shit. The SPY TOOL WhatsApp needs to go down the tube to hell like Apple and their bricking of older models.
Have a day and do it 4 teh LULZ!!!
You just got some real knowledge. Maybe
you'll buy me a coffee?
![]()
![]()
![]() Кто на самом деле владеет Яндексом? (Who really owns Yandex?)
Кто на самом деле владеет Яндексом? (Who really owns Yandex?)
2022 Update: Yandex Source Code
Опубликовано 10 мая 2011 в События
http://superinvestor.ru/archives/6547
Компания Яндекс (точнее, нидерландская Yandex N.V.) опубликовала цены, по которым собирается размещать свои акции на американской бирже Nasdaq. Капитализация компании должна составить $6,4-7 млрд, она предложит рынку новые акции, а часть существующих акционеров продаст свои бумаги.
Деловые издания поместили эту информацию в сегодняшних выпусках, сопроводив её «справками» о том, кто на данный момент владеет акциями Яндекса. Очень жаль, что ни уважаемый Коммерсант, ни уважаемые Ведомости не попытались хотя бы немного критично посмотреть на цифры, перепечатанные из документов Яндекса, опубликованных на сайтах биржи и американской Комиссии по ценным бумагам.
Дело в том, что эти цифры, отражающие якобы текущее распределение акций Яндекса среди инвесторов, довольно далеки от реальности. Нет, Яндекс не обманывает американские власти, биржу и будущих участников IPO (попробовал бы он). Просто компания немного «хитрит», показывая в очень простой и понятной табличке одни цифры, а во множестве комментариев и сносок, набранных мелким шрифтом и написанных зубодробительным «юридическим» английским - совсем другие. Пресса, естественно, клюёт на простую табличку и ленится читать мелкий шрифт. Поэтому СуперИнвестор.Ru представляет более подробный обзор данных, предоставленных компанией.
Ошибка
В форме F-1, представленной компанией перед IPO, на страницах 122-123 есть табличка, в которой указаны нынешние акционеры Яндекса и их доли. Под этой табличкой - несколько сносок-пояснений, которые на самом деле довольно сильно меняют представление о распределении долей. Давайте сначала посмотрим на картинку с этой табличкой:

Обратите внимание на два числа, подчёркнутые красной чертой. Они
показывают количество акций класса B, которыми владеет Чарльз Райан, и
долю этих акций в общем количестве акций класса B. Если исходить из
того, что написано в столбце процентов, то г-н Райан — один из
крупнейших акционеров Яндекса, имеющий «вес» больше, чем сам г-н Волож,
ведь акции класса B имеют десять голосов на каждую по сравнению с одним
голосом акций класса A. Сенсация? Нет. В следующем столбце мы видим, что
г-н Райан контролирует всего 4,06% голосов — чуть меньше, чем у Ильи
Сегаловича и, конечно, намного меньше, чем у Воложа.
Да и буквально строчкой выше стоит Елена Ивашенцева, которая «контролирует» (ниже мы разберём, почему в кавычках) аж 52 млн акций класса B или... 24%, почти столько же, сколько (якобы) г-н Райана. В обоих случаях речь идёт о совершенно одинаковых акциях одного класса, поэтому одинаковая доля должна означать одинаковое количество этих акций. Но у г-на Райана их всего 8,4 млн штук.
В чём же дело? Давайте разделим количество акций класса B Чарльза Райана (8426821) на общее количество акций класса B (оно указано выше по тексту и составляет 215953241 штука). Получим 3,90%. Что очень похоже по написанию на 23,90%, указанные в табличке.
Проще говоря, в одной из самых важных таблиц очень важного документа, который Яндекс и инвестбанки готовили несколько месяцев, присутствует грубая ошибка. В принципе, она может ввести в заблуждение не очень внимательных инвесторов, что может стать поводом для исков к Яндексу. Или, по крайней мере, привести к серьёзному скандалу. Кстати, судя по реакции представителя Яндекса на моё сообщение об этом факте, я был первым, кто обратился с этим вопросом в Яндекс. Остальные или не заметили, или решили посмотреть, что получится.
Но это мелочи по сравнению с тем, что мы увидим дальше.
Базис и надстройка
Давайте прочитаем мелкий текст в сносках к упомянутой таблице и попробуем разобраться, что он означает. Читайте, пожалуйста, в оригинале, по-английски, чтобы случайно не стать жертвой моего возможно неправильного перевода.
Исследование таблицы и сносок показало, что хитрые инвест-банкиры, составлявшие этот документ, несколько раз учли одни и те же акции, представляя их владельцами то одного акционера, то другого. Ключевой собственник Яндекса — группа инвестфондов Baring Vostok Private Equity Funds. Но их доля с точностью до одной акции совпадает с долей партнёра этих фондов, представленного в Совете директоров — Елены Ивашенцевой. Насколько я понимаю, логика такого повторения состоит в том, что в таблице сначала показывают членов Совета директоров, контролирующих (на уровне принятия решений) тот или иной пакет акций (и голосов), а потом — компании, которые формально владеют теми же акциями.
Чтение сносок подтверждает эту догадку. Елене Ивашенцевой просто «приписали» бумаги, принадлежащие Baring. И, как мы дальше увидим, не только ей.
Оказывается, под «вывеской» Baring Vostok Private Equity Funds действует несколько компаний, контролируемых разными группами акционеров. Исследование показывает следующую структуру:

Неплохо, правда? Во всей этой сложной системе есть только одна компания,
которой акции Yandex N.V. принадлежат напрямую. Всё остальное -
«надстройка», призванная скрыть реальных акционеров, но сохранить при
этом за ними право на возможную продажу акций и право голоса (об этом
говорится в сносках). Легко заметить, что даже Аркадий Волож часть своих
акций держит именно в этой структуре.
Кроме Воложа интерес в этой схеме представляет фонд RuNet. Он был одним из первых «внешних» акционеров Яндекса, ещё в почти доисторические времена. Но, как видим, и он «сложил» свои акции Яндекса в общую «копилку» под названием BC&B Holding.
Кстати, ещё один интересный момент. В деловой прессе (см. например Коммерсант) пишут «Runet Holdings Леонида Богуславского». Мы же видим, что как минимум 35,37% его акций (точнее, его «бабушкинской» компании) Internet Search Investments Limited (ISIL) принадлежит компаниям группы Baring. Более того, если мы обратимся к странице 112 документа, поданного в Nasdaq, то обнаружим следующие слова:
Baring Vostok structured and led the initial investment in Yandex in 2000 by Internet Search Investments Limited (the parent of ru-Net B.V.), in which a Baring Vostok fund is the founder and largest shareholder.
Получается, что за ru-Net B.V. (он же ruNet – в документе эти названия взаимозаменяемы, как ни странно) — это структура фондов Baring, а вовсе не Богуславского? Либо, что тоже вероятно, какие-то из «бэринговских» фондов представляют интересы и Леонида Богуславского тоже.
Что такое фонды Baring
Если углубиться в чтение сносок к замечательной табличке, то можно обнаружить интересную вещь. В описании того, что скрывается под цифрами, относящимися к фондам Baring, говорится:
Consists of 16,463,739 Class A shares and 52,199,300 Class B shares held as follows:
by BC&B Holdings
B.V. ("BC&B"): 13,936,109 Class A shares and 23,801,372 Class B shares;
by ruNet BV: 2,527,630 Class A Shares and 28,397,928 Class B Shares.
BC&B holds a total of 33,913,988 Class B shares and 13,936,109 Class A Shares.
Ничего не замечаете? Давайте уберём лишнее, оставив только информацию, касающуюся акций класса B (с акциями класса A там всё более-менее понятно):
Consists of... 52,199,300 Class B shares held as follows:
by BC&B Holdings
B.V. ("BC&B"): ...23,801,372 Class B shares;
by ruNet BV: ...28,397,928 Class B Shares.
В сумме как раз 52,199,300 акций. Но:
BC&B holds a total of 33,913,988 Class B shares.
Внезапно появляются «лишние» 10112616 акций, которыми BC&B владеет, но не в интересах Baring. Что это за акции? Это бумаги г-на Воложа, которые он держит не напрямую, а через компанию Belka, владеющую долей в одной из компаний фондов Baring (Strickland). Т.е. на самом деле распределение акций внутри компании BC&B выглядит так:
- Волож: 0 акций
класса А и 10112616 акций класса B;
- фонды Baring: 13936109 акций класса A и 23801372 акции класса B;
- ruNet: 2527630 акций класса A и 28397928 акций класса B.
Всего эта структура контролирует 16463739 акций класса A и 62311916 акций класса B. При этом акции, принадлежащие ruNet, не являются собственностью BC&B.
Далее. Доля Воложа в компании Strickland (и, в конечном итоге в BC&B) составляет 21,10%. А какова доля его акций в общем количестве акций Яндекса, принадлежащих этой компании? Считаем: 10112616/(13936109+33913988)=21,13%. Удивительное совпадение. Получается, что капитал Strickland фактически сформирован из акций Яндекса, внесённых в него акционерами. Разница в 0,03 п.п. может объясняться например тем, что в капитал вносилась ещё и небольшая сумма наличных (на мелкие текущие расходы) кем-то из акционеров.
Но если посмотреть на структуру владения акциями Strickland, то легко заметить, что фонды Baring разделили свои акции этой компании на три части, передав их трём «бумажным» офшоркам: BVNL, DDNL и CNL. Логично предположить, что эти офшорки представляют интересы трёх групп инвесторов, скрывающихся за структурами Baring (по аналогии с Belka, которая представляет интересы Воложа).
Загадочный акционер
Далее последует не утверждение, а предположение, основанное на чутье и некоторых логичных рассуждениях, которые я здесь опущу. На мой взгляд, компания BVNL представляет интересы нынешних и бывших сотрудников Яндекса, имеющих небольшие пакеты акций класса A. Кроме того, есть ощущение, что в этой же компании «прячется» крупный пакет акций класса B, равный тому, что Аркадий Волож держит в своей Belka.
Давайте попробуем посчитать.
34,30% акций компании Strickland, которые принадлежат BVNL, соответствуют примерно 16412000 акций Яндекса плюс-минус десяток тысяч за счёт ошибок округления и возможных взносов наличными. Согласно имеющейся на сегодня информации, фонды Baring собираются продать 6242000 акций Яндекса класса A. Если мы вычтем из доли BVNL 6242000 акций, то получим примерно 10170000 акций с погрешностью в несколько тысяч акций. Т.е., например, нечто, очень похожее на 10112616 акций класса B. Получается, что доля BVNL с очень высокой точностью (до десятых долей процента) делится на две части: акции класса B в количестве, равном тому, что имеет в фондах Baring Аркадий Волож, и акции класса A в количестве, равном тому, что фонды собираются продать во время IPO.
Если верить в эту теорию, то получается, что в BVNL «спрятан» крупный акционер, владеющий солидным пакетом акций класса B. То есть акций, распределявшихся среди основателей компании и её ключевых долгосрочных инвесторов. И эти акции лежат в одной «упаковке» с акциями сотрудников, что наводит на мысль о том, что и этот акционер — бывший или нынешний сотрудник.
Подчеркну ещё раз, что эта главка — не сведения, полученные из каких-либо официальных или неофициальных источников, а исключительно умозрительные рассуждения, базирующиеся на логике и математике.
Другие акционеры
Дальше всё проще и однозначнее. Сноски к таблице объясняют реальную принадлежность акций, «записанных» на некоторые инвестфонды. Скажем, то, что на первый взгляд принадлежит Kameson Management Limited, UFG Private Equity Fund II LP и Almaz Capital Russia Fund I LP, на самом деле контролируется человеком по имени Чарльз Райан — это бывший главный исполнительный директор Deutsche Bank в России. В общей сложности, на него приходится примерно 15,5 млн акций, из которых около 8,5 млн — класса B.
Интересная история с компанией Roth Advisors — одним из крупнейших владельцев «престижных» акций класса B. За этой компанией стоит семья Кэрол и Курта Рот, живущих недалеко от Чикаго. Курт — инвестбанкир, но, скорее всего, Яндекс вызвал интерес у его жены Кэрол — известной в США деятельницы предпринимательского движения. Она консультирует компании по вопросам стратегического управления, пишет книги, выступает на ТВ, коллекционирует кукол (это просто к слову). А заодно инвестирует в некоторые из компаний, которые обращаются к ней за консультациями. Вероятно, Яндекс в какой-то момент общался с ней, что и стало причиной покупки акций поисковика.
Бен Коул — один из директоров компании с 2000 года. Он активно инвестирует в российские высокотехнологичные бизнесы, в том числе в проекты, связанные с Аркадием Воложем — CompTek и InfiNet Wireless. C InfiNet связан и Роберт Харви Стабблбайн — CEO этой компании. В остальном среди относительно крупных акционеров представлены в основном различные инвестфонды.
Распределение акций Яндекса до IPO. Версия СуперИнвестор.Ru

Ещё порядка 15% акций класса B так и не нашлись. Яндекс либо как-то
очень удачно скрыл их в опубликованных данных, либо просто не раскрыл их
владельцев в документе.
Мелкие акционеры
Яндекс периодически «награждал» своими акциями сотрудников компании. Кроме того, часть сделок по покупке различных бизнесов, вливавшихся в структуру Яндекса, проходила через полный или частичный обмен акциями. Поэтому к настоящему моменту у компании «накопилось» довольно много (несколько десятков) миноритариев, владеющих долями процента акций. С точки зрения процентов и голосов это — несущественная мелочь. Но с точки зрения денег — очень приличный капитал. Если Яндекс разметит свои бумаги хотя бы по нижней границе ($6,4 млрд), то 0,1% акций будет стоить больше $6 млн. Кто же они, миллионеры Яндекса?
Частичный ответ на этот вопрос есть в форме, представленной в Nasdaq. Насколько я понимаю, там не все акционеры, но большинство. Ниже вы можете увидеть этот список.
Амилющенко Алексей
Валерьевич — бывший главный аналитик Яндекса, сейчас работает в Google;
Андронова Валентина Павловна — нет информации;
Бадера Олег Алексеевич – глава компании-разработчика Яндекс.Пробок;
Чебунина Елена Владимировна — нет информации;
Достов Виктор Леонидович — директор по развитию компании PayCash
(базовая технология Яндекс.Денег);
Фадеев Михаил Александрович — директор Яндекса по системному
администрированию;
Фельман Дмитрий Павлович — руководитель отдела в компании КомпТек;
Голдинг Павел Юрьевич — нет информации;
Ильинский Сергей Владимирович — руководитель группы в Яндексе;
Исаев Артур Александрович - генеральный директор ОАО «Институт Стволовых
Клеток Человека», соинвестор в проекте Яндекс.Пробки;
Иванов Владимир Леонтьевич — нет информации;
Иванов Дмитрий — директор по проектам Яндекса;
Мазуров Алексей — руководитель департамента разработки Яндекса;
Хуцян Мария — нет информации;
Колмановская Елена Савельевна — главный редактор Яндекса;
Котеров Дмитрий — сооснователь проекта МойКруг;
Положинцев Илья Димитриевич — исполнительный директор Сравни.ру,
экс-руководитель направления электронной коммерции Яндекса;
Тейблюм Дмитрий Михайлович — разработчик в Яндексе, один из старейших
сотрудников;
Уманский Илья — нет информации;
Третьяков Алексей — коммерческий директор Яндекса;
Шульгин Александр — финансовый директор Яндекса.
![]()
![]()
![]()
Suggested reading:
http://www.jar2.com/topics/CIA.html
http://www.jar2.com/Topics/Google.html
http://www.jar2.com/Topics/Snowden.html
http://www.jar2.com/Articles/2016/July/The_Truth_About_Crimea.html
http://www.jar2.biz/Downloads/Books/Full_Spectrum_Dominance.zip
January
24, 2019
- During the lesson someone mentioned Operation Snowden and Cognitive
Dissonance. If you are really interested in the issue and Cyber Security
then I suggest you read the above articles and essays to study up on the
subject. Cheers and good reading and listening.



![]()
![]()
![]() USA is Involved in Offensive Cyber Espionage - Joseph Fitsanakis.
USA is Involved in Offensive Cyber Espionage - Joseph Fitsanakis.
26 June, 2013 17:55
According to the Chinese state-run newspaper Washington is again playing the victim. This time the evildoer is not Russia but China. And the victim – Washington – is being victimized by cyber espionage, when, in fact, according to the Chinese newspaper, it is the world’s top intelligence power.
"Regarding the issue of network security, the US is such a mincing rascal that we must stop developing any illusions about it" – wrote the Global Times.
On Monday the US Grand Jury indicted five Chinese military officers on charges "they broke into US computers to benefit Chinese companies" in the first ever prosecution by Washington of state actors over cyber espionage.
Beijing responded furiously on Tuesday, summoning the US Ambassador Max Baucus and accusing Washington of double standards. Authorities also banned the use of Microsoft’s Windows 8 operating system on all new Government computers and suspended the activities of the bilateral cyber working group.
The Global Times said that Washington's "pretentious accusation against the Chinese army officers is ridiculous" given that the US NSA itself has engaged in widespread cyber spying through its PRISM program.
Interpol, according to the Chinese publication, "should have ordered the arrest of designers and implementers of the PRISM program but they did not". "Therefore the US is acting so shameless by posting photos of the five Chinese army officers."
The US prosecutors said the five indicted officers belong to Unit 61398 of the People’s Liberation Army.
A report last year by the US security firm Mandiant said the unit had thousands of workers operating from a nondescript 12-storey building on the outskirts of Shanghai and that their goal was to pilfer intellectual property and government secrets.
Beijing has denied the accusations and the Global Times on Wednesday called them "beyond our imagination".
INTERVIEW
Hello! This is John Robles, I’m speaking with Pr. Joseph Fitsanakis. He is the coordinator for the Security and Intelligence Studies Program at King University, and the Director of the King Institute for Security and Intelligence Studies. He is also the Senior Editor at Intelnews.org.
Hello Sir! How are you this evening?
I’m great! How are you?
I'm pretty good myself. I read your article that you wrote about the scandal going on right now between China and the US regarding cyber spying. I’d like to ask you about the unprecedented charges against the officials, the naming of officials. Is the US really just a victim in all this?
First of all, let me agree with you – this is absolutely unprecedented. This is obviously an FBI operation. The FBI is the American intelligence agency in charge of counterintelligence. And we’ve never heard of the FBI actually naming the Chinese officials for People’s Liberation Army as persons responsible for espionage against the US.
These charges are indeed unprecedented. And some people think they maybe shape the things to come.
The timing of this! Now, when President Putin is in China, the Chinese-Russian relations are moving ahead quantitatively. What about the timing of this? Do you think this is specially timed?
We will see as the Chinese-Russian relations move ahead. I mean, it all depends on whether the deal with gas exports is going to be signed between the two sides.
The timing, of course, we can read all kinds of things in the timing. The US accuses China of economic espionage. That pushes China away from the US and to Russia. So, I’m not sure that will be too much in the timing of this, at this moment.
I don’t know if the US is interested anymore in doing business with anybody or having normal relations. I mean, they are pushing Russia away, they are pushing Europe away. Why not China?
That’s an excellent question. Some officials may not be accountable at all with this revelation. However, often the FBI will say – you know, I don’t care what do you think, the fact is that we have a counterintelligence investigation at hands, we have these officials that have been named, it is our duty to go ahead and name those officials.
I have a problem with a lot of the US media right now, especially with the coverage of Ukraine. I mean, it is all self-serving. And of course, they are going to demonize China as much as they can right now, because it has closer relations with Russia. And it seems like, as far as the media goes, anything they can do to demonize Russia in the last half a year intensely, they are going to do it.
This is not necessarily a controversial argument that you are making. I mean, the fact is that the American-Russian relations are not in a very good state right now. This revelation or this accusation just seems to appear out of the blue. So, yes, you are making a good point here.
Okay, in your article the headline was The US Cyber Security Posture is not Purely Defensive. What did you mean by that?
The US for the last decade or so has made the point that it finds itself unfairly targeted by the foreign cyber espionage. The question that one has to ask, and I’m speaking purely academically here, is – to what extent does the US itself is involved in offensive cyber espionage. Because one thing is to be defensive in the posture, and another thing is to be offensive.
And I think a lot of us who study this for living have this impression that the US is also involved in offensive espionage. We have had some evidence in the past of cyber security experts at the State Department who have attacked the websites.
What about Stuxnet?
If the US or other Western countries have an involvement with Stuxnet, that will be a textbook example of not cyber espionage, but cyber sabotage, if the US does that.
And here, there is an important issue, because every country in the world at this moment, they only say that they are defending themselves. I'm not quite sure this is accurate. I don’t pay too much attention to these crimes.
But what about Edward Snowden’s revelations? Are you going to say all that is lies or what?
The Edward Snowden’s revelations I think made a big impact on how we think about cyber espionage. The revelations themselves have shown that the US has spied on, particularly, foreign countries like Germany, Brazil etc.
I would take a step further – one the most incredible espionage revelations by Snowden didn't concern the US. It concerned spying by Australia against East Timor – a mining company for a mining contract which had nothing to do with the Australian national security, but had a lot to do with Australian economic interests. And Australia is considered as an analog of the US and Western countries. A very much shameful episode in the Australian intelligence’s history.
So, yes, I think the Snowden’s revelations have shed a lot of interesting light on how nations behave in the cyber realm.
In your article you’ve mentioned Hilary Clinton. She said that "countries or individuals that engage in cyber attacks should face consequences and international condemnation". That is everybody except for the US, as I take it.
Right! Again, you know, it is interesting. The US is very vocal about finding itself a victim of cyber espionage operation. I'd imagine that there is a cyber offensive aspect to America’s online presence.
So, in fact, what is interesting about this current spat with China, is that the US has said, in fact, many American officials have said that America does engage in espionage. But one thing they want to make clear is that the US does not engage in economic espionage. That what separates us from China, is that we don't spy on companies.
I’m sorry, I wasn’t born yesterday. I mean, I can’t believe that. The EU had all this evidence that they were spying on economic bodies in the EU and this stuff was brushed under the carpet really fast by the US Government.
That’s the argument the US makes. Now, I remember back in the mid 1990s, when the Echelon network revelations came out, at that point any European countries, particularly Germany and France, were very upset believing that the US has engaged in economic espionage against their companies.
In fact, at that time, around 1998 or 1997, the EU sent a delegation to America to investigate these claims that were made in official EU report. At that point the US officials refused to meet with them.
So, like you, I was not born yesterday and I don’t disagree with your skepticism that that may well be.
I know and I’m sure you know there is a very-very close relationship between the US corporations, the military industrial complex, the big oil companies, these private intelligence companies in the US. This is not right! This is almost an incestuous relationship between these huge moneyed interests in the US Government and the intelligence community. So, I take that you agree with me that the US is not just innocent here.
To find innocence…almost every country in the world engages in offensive cyber espionage. And it would seem logical to assume that every country is either engaged in offensive cyber espionage or is exploring ways to become engaged in offensive cyber espionage.
That’s of course purely a conjecture using common sense, because I have no evidence to show this. But I think using common sense we have to assume that every country is engaged in this field of intelligence in some way or another.
What about the level of the intrusiveness of the NSA, for example? They’ve crossed some lines that shouldn’t have been crossed. I mean, spying on American citizens in the US, collecting information, that really they have no right to, from innocent people and I’m sure form companies etc. I mean, it is just within the US, don’t you think they’ve crossed the line?
If you ask the NSA, they will tell you that mistakes happen and so on and so forth. My personal view is that when you are looking at intelligence agencies like the NSA, comparatively speaking the NSA is more transparent in its operations that other similar agencies in the Western world, including by the way the British GCHQ…
The NSA is more transparent? They didn't even exist a few years ago.
Exactly! The joke that NSA stood for No Such Agency. Keep in mind that both authorized and unauthorized revelations about the NSA going are back to the late 1980s…
So, would you say that Snowden’s revelations were authorized? I think they weren't. That's why they were so ballistic.
Absolutely not authorized. And I don’t think there is any intelligence observer that would not agree with the statement that the Snowden’s revelations were very damaging.
I wouldn't say they were damaging for national security. They didn’t damage any security, they just verified what everybody already knew.
But think about, for example, the case of the US relations with Germany. They have been actually quite hurt by the revelations.
So, it should be okay that the US was spying on Germany?
The world of intelligence has its own rules. We are not talking about the department of agriculture here. These agencies and these functions go to the core of the modern nation state. And so, this is by nature very-very secretive. And I don’t think that is going to change any time soon.
The US nation state is at its core super secretive. And anybody who exposes anything that they are doing is demonized, like Bradley Manning, Edwards Snowden.
Yes! And closer you get to the core functions, for example, the national security and defense, the more secrecy is apparent.
And about Snowden, let me remind you that Snowden's revelations were not that shocking in many ways. But I think our conversation began me talking about America and China, rather than domestically. I think those two things are not necessarily related.
It is a continuation of – we are being attacked, we are innocent, we need to step up security, we need more millions of dollars for security, because we are being threatened.
America spends more on its defense that the rest of the world combined.
There is nobody threatening the US militarily.
Let me point this argument to you. If I were China, if I were Russia, I would realize it will be quite difficult to compete with the US in conventional warfare.
You've just made a mistake most Americans make, that there is no competition. The US is overextended. Really, the US officials and, apparently, most American people think that you have an unbeatable army and military force that is going to force American hegemony on the entire planet. It is not going to work.
Yes, I don’t think the recent history shows that the American army in unbeatable. In fact, if anything, there are several problems with its ability to dominate the battlefield.
The problem with this argument – it is more dangerous for Americans, because they are going to go out there and die with this false idea in their heads. It is a big disservice to the American people and to soldiers, and to anyone in the military.
It was actually quite interesting when the US went into Afghanistan, many articles appeared in the international press by the former Soviet veterans who were basically sharing their experiences of the war in Afghanistan and in many ways actually warning the US about what they are going into.
That war in Afghanistan would have been one interesting aspect in which, perhaps, Russia and the US could have worked together.
The people running everything, they are not thinking that way. And that is a problem. They are not thinking the way a normal person would. As far as I see it, they are provoking everybody on the planet. And now they are going to provoke China. I get this real impression that they are trying to start WW III in Ukraine.
When you say they, you know, it is very-very difficult to pinpoint who they are.
They keep themselves in the shadows and they've been in the shadows since 9/11.
This is John Robles, you were listening to an interview with Pr. Joseph Fitsanakis. He is the Senior Editor at Intelnews.org. He is also the coordinator for the Security and Intelligence Studies Program at King University, and the Director of the King Institute for Security and Intelligence Studies.
![]()
![]()
![]()
29 June,
2013
04:08

In what
can only be described as an assault on freedom of speech and access to information,
the U.S. Government has made the decision to block and filter internet access
to the site of the U.K.’s Guardian on its U.S. Army networks, with the revelation
coming to light after complaints from soldiers at the Presidio in San Francisco,
California.
According to the Voice
of Russia one
Gordon Van Vleet, a spokesman for the Army Network Enterprise Technology
Command, or NETCOM, stated that press coverage and online content about
NSA leaks is being filtered and blocked.
Media
reports say the blocks do not only apply to the facility in San Francisco
but that they in fact cover the entire global U.S. Army network and while
this is supposed to prevent U.S. Army personnel from accessing data that
is available to the rest of the planet (more or less) it is not preventing
them from viewing the information on their cell phones or their personal
laptops or computers at home.
The hypocrisy
here seems self evident. Here we have the people that are supposed to die
for America and they are not allowed to view information concerning their
government that is available to everyone else. The claims that the Department
of Defense has made that the documents and the information on the PRISM
program that are available online are classified and therefore can not be
shown on unclassified sections of the U.S. military network seem plausible
and credible until you consider that the information is now in the public
domain and anything that was “classified” about it can no longer be the
case.
While
this is preventing soldiers from accessing the information on the PRISM
program, surely one of the biggest revelations in the last several years,
it is also preventing, or attempting to prevent soldiers from viewing or
taking part in the debate and viewing the reaction from Americans and the
world on the matter.
The fact
the U.S. Government is attempting to censor what is viewed by American soldiers,
people who are supposed to be ready to give up their lives to protect the
American people and that very same government, throws the unbelievable arrogance
of the United States once again, right out there for the world to see. It
is also an indication of the almost lunatic level that the U.S. Government
is going to in its attempts to hide its own illegitimacy and criminality
from the American people, a people whom they are supposed to serve.
Like the
assault on whistleblowers and anyone who attempts to expose the thugs in
Washington and the criminality of the U.S. Government, this attempt to keep
soldiers in the dark and dumbed down just adds to the overall mosaic of
illegitimacy that the U.S. continues to paint of itself for the eyes of
the world to see.
Of course
from a command point of view it is not expedient that the troops on the
ground and GI Joe and Jane know that the government that they are serving
and that they must be ready to make the ultimate sacrifice for is no longer
a legitimate government adhering to the constitution that they are all sworn
to protect and must also be ready to die for.
The criminal
cabal that has taken over the United States Government, under the control
of the biggest criminal of all sitting in the U.S. White House, has proven
time and time again that the law only applies to those that it itself determines
they apply to. The unapologetic, arrogant and absolutely remorseless and
conscienceless way that the extra-judicial executioner in chief and the
government react to revelation after revelation is as frightening as it
is nauseating.
The PRISM
revelations which should be a damning indicator on the true state of the
U.S. Government and which have proven that the entire terror paradigm is
a complete and utter fabrication and has been since day one, have once again
shown that the illegality that has been exposed and the egregious violations
of law and the U.S. Constitution that are being uncovered on a regular basis,
mean nothing to those in power who are committing them.
The criminal
cabal calling the shots in the United States from the Kingpin in the White
House to every single one of his henchmen, are all above the law and have
become a law unto themselves.
The sanctimonious
and hypocritical way that they go on and on dictating to the world about
freedom, justice and human rights and pursuing policies dictated by double
standards is becoming ever the more laughable with each and every passing
day.
The fact
that they are facing worldwide condemnation for their global spying network
has not fazed them in the least, like a huge bully with an IQ of 40, rather
than making corrections to their behavior they continue to employ the only
tool they have, a sledgehammer. A sledgehammer which they continue to employ
brutally against anyone they see as a threat to their own endless power,
power they believe is absolute, but as absolute power corrupts absolutely,
in the end it also destroys absolutely.
PRISM
was created to control the world, it is illegal an abomination and must
be shut down, however those controlling it are blind in the greed for control
and power and now, rather than admitting they are wrong they will continue
to snub their noses at all of us continue to violate international law and
international norms right in our faces.
Normally
the bad child caught with his hand in the cookie jar pulls his hand out
and apologizes to his mother. This child has grown insane with its own power
and instead picks up the cookie and brains his mother with it so he can
continue eating the cookies he has no right to.
Illegality, subjugation, invasions, destruction, spying, assassinations, droning and a relentless mindless effort to bring the world to its knees and to achieve complete and total control over every single person on the planet are what we can expect from the U.S.. Or is it?
![]()
![]()
![]() PRISM: Every move you make, “they” will be watching you
PRISM: Every move you make, “they” will be watching you
26 June,
2013
17:55
The US
Government and the unified global communications network operated by an
alliance of the secret SIGINT units of Australia, Canada, New Zealand, the
United Kingdom and the United States called UKUSA, has developed, expanded
and spread unhindered to such a point that everything and anything you do
on the internet, on a cell phone and through every other means of electronic
based communications can, and now we know, is being collected, recorded
and spied upon.
Like United
States military infrastructure, through its international global military
arm NATO, U.S. signals intelligence operations have now spread to every
corner of the globe and are greedily gobbling up anything and everything
that is flowing through cyber space, regardless of its origin or the rights
of those being spied upon.
Two points
are important to recall here, one that the Internet that we all so love
and use and which has taken over the way the world does business and exchanges
information was initially a U.S. global military network, and two that the
expansion of the surveillance of the Internet to today’s present level and
form was made possible by the “War on Terror” paradigm which has existed
since 9-11 and has cowed most of the world’s population into fearful submission
allowing the security services to expand their scope with almost complete
and unhindered impunity.
Despite
the reported efforts of the Global Network Initiative, a non-governmental
organization (NGO) with the stated goals of preventing Internet censorship
and protecting the Internet privacy of individuals there has been little
that they have been willing and/or able to effectively do against the massive
expansion and scope of spying programs being run by the National Security
Agency (NSA) and the United States SIGINT System (USSS).
According
to open source intelligence the PRISM SIGINT Activity Designator (SIGAD)
replaced the post 9-11 Terrorist Surveillance Program (TSP) which was operating
illegally without the approval of the Foreign Intelligence Surveillance
Court (FISC). However such programs, once the foundations and infrastructure
are in place and if they have proven to be effective, may just be temporarily
closed and re-launched using different names, locations, personnel and financial
and administrative bodies and methods to hide and obfuscate their existence
and true nature.
Hence
programs like TSP, ECHELON, CARNIVORE may be shut down, paused and then
restarted and repackaged and renamed. PRISM is the likely product of such
projects and the unification of platforms across the SIGINT intelligence
operations sphere. PRISM was approved by the U.S. judiciary and hence has
been operating with impunity since at least 2007, controlled and operated
by the Special Source Operations (SSO) unit of the United States National
Security Agency (NSA).
PRISM
is just the tip of the iceberg and is just a small part of the U.S. Government’s
mechanism for spying on and controlling the countries and the peoples of
the world. I mentioned the UKUSA group, their efforts are also worth noting
What about the other partner countries in the spying alliance? Are they
innocent of such egregious spying? Yes they are and even worse because they
pass the private information of their citizens to the United States.
In this
article I am dealing with Signals Intelligence (SIGINT) as it effects the
average citizen of the world, this in no way means that the programs and
the methods that I am discussing are by far the only instruments they are
using to dominate the globe, all allowed and tolerated in the name of security.
SIGINT involves many different intelligence collection instruments and methods
and with the recent advances in technology these have grown incredibly.
The basic areas of SIGINT can be grouped into two broad categories: communications
intelligence (COMINT) and electronic intelligence (ELINT). As technology
advances the crossovers and combinations of the two grow by the day, meaning
for example information from a Skype chat would fall under both COMINT and
ELINT, not a fact of vital importance but one that should be noted.
The members
of the UKUSA Security Agreement: Australia, Canada, New Zealand, the United
Kingdom, and the United States, are also referred to by a number of abbreviations,
further obfuscating their nature and existence such as AUSCANNZUKUS and
Five Eyes. All of these countries are members of the ECHELON spy network.
Which was originally, like NATO a program set up to spy on the former USSR
and the Eastern Block and has been expanded, like NATO, at an incredibly
rate since the end of the cold war and the collapse of the Soviet Union.
Gone are
the days when the CIA would spend years attempting to dig tunnels and splice
into the telephone networks of Soviet cities. Today they are connected to
absolutely everything and anything. According to a report on ECHELON it
is capable of intercepting telephone calls, faxes, e-mails and other data
traffic worldwide including satellite based transmission, public switched
telephone networks (which once carried most Internet traffic), microwave
links, fiber optic communications and cell phone line of site networks.
With the
revelations of the PRISM program which they say has been operating since
2007 it is now evident that the data collection capabilities include: e-mail,
voice and video chats, streaming and other video, any and all photos, stored
data on your hard drive, voice over IP (VoIP) conversations, file transfers,
notifications of logins, etc., social networking details and a special category
called “special requests”.
If we
throw in satellite surveillance, CST systems, RFID chips, cell phone location
and usage monitoring including interception of text messages, automobile
tracking devices, credit card and purchasing information collection and
GPS device related transmissions, then almost everything you do is subject
to surveillance and monitoring, in a nutshell this means the spooks can
now find out what you had for dinner last night, with whom and how much
you paid for it, as well as every other private aspect of your lives.
United
Kingdom
The U.K.’s
programs are more hidden than those of the U.S. and there is less information
available about them either because they are better at hiding them or they
are less in number but their scope is almost equal to that of the U.S. however
they are more restrained than their American “special friends”. We know
that the U.K. is an active member of the ECHELON based infrastructure and
now we know that they are also active in the PRISM SIGINT Activity Designator
(SIGAD), or simply PRISM.
There
are still calls from people like Stella Rimington for the expansion of U.K.
spying so it is possible that the U.K. is lagging behind their American
friends although judging by the number of CCTV cameras in London this is
doubtful.
As for
data collection stations the main ones for the United Kingdom are the Menwith
Hill (US) facility, the Aiyos Nicolas Station in Cyprus and of course GCHQ,
the U.K.’s version of the NSA. Again there is little information available
on specific programs, which come under the aegis of directorates of Military
Intelligence and GCHQ.
A little
known fact about the U.K.’s Military Intelligence is that they have at least
20 directorates that are known about. With regards to SIGINT these might
be handled by MI-1 (codes and ciphers), MI-5 and 6, MI-8 (signals and communications),
MI-10 (technical), and perhaps MI-13 which like the NSA until recently doesn’t
exist.
Australia
Although
you may have thought Australia might be behind when it comes to the level
of its secret bureaucracies and the amount of spying it does think again.
Among entities in Australia that provide for governance and policy over
the secret service and operations are: the NSC, the SCNS, the NCTC, the
NICC, the NICMC, the NIOSC, the HIAM, the NSIPC, the NSA (not that one),
the DNSA, the NSCIO, the ISD and more.
Intelligence
agencies include the Australian Security Intelligence Organization (ASIO),
the Australian Secret Intelligence Service (ASIS), the Defense Intelligence
Organization (DIO) and but not limited to, the Defense Signals Directorate
(DSD). However it is probably the DSD that we are most interested in as
they handle the analysis, collection and distribution of foreign SIGINT
and are responsible for communications, information, cyber and computer
security.
Their
main global station is located right in the center of Australia at Pine
Gap but they have stations throughout Australia.
Canada
Canada’s
Security Intelligence Service (CSIS) in not only part of the UKUSA group
but shares intelligence with the U.S., the U.K., and Australia under what
is called the “Quadpartite Pact”. CSIS is the principle Canadian intelligence
service and are a civilian service unlike the MIs and the NSA and CIA. However
Canada’s Communications Security Establishment Canada (CSEC) is responsible
for SIGINT in Canada.
CSEC has
facilities at CFS Leitrim, the main SIGINT facility, and at other locations
such as CFB Gander Newfoundland, CFS Masset, BC and CFS Alert, Nunavut.
CSEC relies
mainly on the U.S., U.K., Australia and New Zealand for its intelligence
collection and benefits substantially from UKUSA, especially when it comes
to foreign communications.
Currently
Canadian programs are still largely secret although involvement with PRISM,
ECHELON and other programs has been documented, to what level they provide
the CIA and the NSA information on Canadians remains to be seen.
New Zealand
The Government
Communications Security Bureau (GCSB) listens to phone calls and intercepts
e-mail and other communications but is not supposed to do so on citizens
of New Zealand, they have been reported to be a part of ECHELON.
New Zealand
Security Intelligence Service (NZSIS or SIS) is responsible for foreign
intelligence operations and information gathering. However it is the super
secret Combined Signals Organization (CSO) that handles SIGINT, ECHELON
operations and the like.
PRISM
operations in New Zealand would fall under the GCSB and the CSO, but again
their level of participation may be minimal and due to New Zealand’s small
size they are more likely largely beneficiaries of UKUSA and PRISM operations.
![]()
![]()
![]() The “Real Hacking Empire” and the War on Truth
The “Real Hacking Empire” and the War on Truth
12 May, 03:45

The cyber
war continues, with the People’s Republic of China and the United States,
trading accusations of cyber attacks, but the real war is a war to control
and manipulate information and to keep the “inconvenient truth” from reaching
the world’s internet denizens. A sign of an empire in decline is the stifling
of truth that shows its illegitimacy and a war on those who would expose
the truth. Attacks on China have to be seen as part of a larger US effort
and the next victim could be anyone.
Back in February we reported on a
cyber security firm called Mandiant,
in Alexandria, Virginia, less than half an hour from the unincorporated
community of Langley (the metonym for the CIA) in McLean, Virginia. The
firm had made public a report detailing threats posed by Chinese hackers.
They claimed the “Advanced Persistent Threat” (APT), actors operating in
China and with the blessing of the Chinese Government, had been conducting,
quote: “… a cyber espionage campaign against a wide range of victims since
2006” unquote.
I took
them to task for their self-serving claims, their security suite according
to SC Magazine, called “Mandiant Intelligent Response”, which will protect
anyone from Chinese super hackers costs $86,000.00. I also took them to
task for the amount of surveillance and penetration of Chinese government
sites and Chinese internet infrastructure, the level of which was astounding.
Just to produce the report they released they had to launch their own massive
penetration campaign and hack into thousands of Chinese sites and systems.
So the
recent claims by the Chinese Government, after the Pentagon released a report
accusing China of launching cyber attacks, that the United States of America
is the “real hacking empire” and has “an extensive espionage network” are
not surprising in the least and I would say a given.
In a recent article
on the matter the website Quartz details
some of the ways in which the US hacks into the systems of other countries.
Quartz wrote: “The
US has some of the most powerful cyber warfare resources in the world and
has long been one of the leading sources of cyber attacks on companies and
people. According to cyber security firm McAfee, the US is home to the largest
number of botnets in the world, the control servers used to hack computers
in the US and elsewhere. Data from Deutsche Telekom shows that far more
attacks against its networks come from Russia and the US than China. And
according to HostExploit, which tracks malware activity, the US and Russia,
not China, have the world’s most malicious servers.”
They also wrote: “In
some ways, Beijing is right to argue that China is also a victim, wrote
Jason Healy, director of Cyber Statecraft at the Atlantic Council, last
month. Between September 2012 and March of this year, 85 Chinese government
and company websites were hacked, with 39 of the attacks originating in
the US, according to Chinese state media. Chinese authorities also said
that US-based servers had hosted 73% of phishing attacks on Chinese residents
during roughly the same period.”
This is
all not surprising as the US continues to attempt to control the flow of
information worldwide, wage a war on whistleblowers and shut down resources
and silence people who go against the official US line or expose the criminality
of those in Washington and the United States. Along with the illegal global
war on terror and all of the crimes being committed in its execution and
the global military expansion by the US through its surrogate NATO, the
United States had proven that it is the single biggest security threat in
the world, not only a threat to freedom of speech and expression on the
internet, but even more importantly to world peace.
Although
many of the world’s internet denizens see the internet as a wonderful source
of information and a way to share information and reach out to others, governments,
particularly the US, which created the internet in order to hide a military
computer network, see the internet as a tool to collect intelligence on
foreign governments and on the world’s populace. One reason Facebook has
a special CIA interface.
Some of the aspects of this militarization of
the net and the war on information activists and whistleblowers by the US
government were chillingly described by Julian
Assange in a recent interview he gave to the Nation.
Mr. Assange remains trapped in limbo in the Ecuadorian Embassy in London
and will soon mark his one year anniversary there as the UK authorities
refuse to grant him safe passage to the airport in a continuing violation
to international norms and diplomatic etiquette.
According to however the US has lost: “The
status quo, for them, is a loss… The Pentagon threatened and me personally,
threatened us before the whole world, demanded that we destroy everything
we had published, demanded we cease ‘soliciting’ new information from US
government whistle-blowers, demanded, in other words, the total annihilation
of a publisher. It stated that if we did not self-destruct in this way that
we would be ‘compelled’ to do so.”
… effectively
exposed the empire’s hypocrisy, indiscriminate violence and its use of torture,
lies, bribery and crude tactics of intimidation. shone a spotlight into
the inner workings of empire (the most important role of a press) and for
this it has become empire’s prey. Those around the globe with the computer
skills to search out the secrets of empire are now those whom empire fears
most. If we lose this battle, if these rebels are defeated, it means the
dark night of corporate totalitarianism. If we win, if the corporate state
is unmasked, it can be destroyed.”
The persecution of the recent shut down
of the Cyber Bunker, attacks on Chinese, Russian, North Korean, Syrian,
and Palestinian servers and web sites show just how concerted the efforts
are by the US in attempting to control the flow of information worldwide.
With regards to alone the Nation said: “At
least a dozen American governmental agencies, including the Pentagon, the
FBI, the Army’s Criminal Investigative Department, the Department of Justice,
the Office of the Director of National Intelligence, and the Diplomatic
Security Service, are assigned to the case, while the CIA and the Office
of the Director of National Intelligence are assigned to track down supposed
breaches of security.”
Rather
than hunt down the criminals exposed by the whistleblowers they continue
to attempt to go after the messengers of truth and control the world’s flow
of information.
In the
context of China, I think it is important to recall that China is a working
and successful Communist country, something the US is usual quiet about
as China’s economic stake in the US is so large that if it pulls out the
US would no doubt collapse, and geopolitically China along with Russia are
seen as enemies by Washington, so it is a given that the US will try to
do anything it can to undermine not only China but Russia and any other
country it sees as a challenge. That the single largest military threat
to the planet and the world’s policeman and censor is also the “real hacking
empire” is not surprising.
![]()
![]()
![]() CyberBunker - Spamhaus battle leads to largest DDoS attack in Internet history
CyberBunker - Spamhaus battle leads to largest DDoS attack in Internet history
28 March,
2013
19:19
It has
been identified as the largest DDoS attack in the history of the internet,
at one point reaching a mind boggling 300,000,000,000 bits a second, that’s
billion (300Gps), and it has affected servers, websites and web services
all over the net, slowing down the net and making some sites completely
inaccessible.
Once again
we see violent opposition to mediocre minds trying to control the internet
and tell you what you can see and what you can not see, who is bad and must
be shut down, and who should be allowed to speak. The internet was one of
the few mediums where is information was free, however more and more we
see attempts to limit and control the flow of information. We have even
recently seen information activists become the subject for western military
attack. One provider which offers access to anyone free of censorship
is under attack and the net has decided to fight back.
The attack
is part of an ongoing battle for internet freedom between supporters of
a provider name CyberBunker, which provides uncensored hosting for everything
and anything, except for child pornography and terrorism, and a company
called Spamhaus which claims to be battling spam but which has effectively
become an internet censor by arbitrarily blocking entire domains and providers
under the cover of battling spammers.
At the
heart of the cyber war between backers of CyberBunker and Spamhaus is the
fact that Spamhaus placed the provider on a blacklist, and has effectively
been blackmailing Internet Service Providers (ISPs), ISP providers and carriers
into disconnecting clients and web services with a court order or legal
redress.
In October
of 2011 Spamhaus single-handedly determined that Cyber Bunker was a “haven
for spammers” and asked A2B, which is their upstream provider, to cancel
their internet service and disconnect their servers.
If Spamhaus,
which claims to be a non-profit organization and is used by millions to
filter internet traffic and e-mails every day, determines that a domain
or provider is being used to send spam, Spamhaus adds the domain or, in
this case, the entire provider to its blacklist, hence cutting them off
from the net and their users. ISPs know this and are then forced to censor
or cut off their clients, again without legal recourse or a legal order,
just because Spamhaus says so.
CyberBunker,
which is housed in a real bunker; a five-story-deep ex-NATO cold-war-era
bunker that was designed to withstand a nuclear attack, located near the
town of Kloetinge in the Dutch countryside in the southern part of the Netherlands,
says they are not responsible for the attacks but that a consortium of ISP
and carrier organizations and thousands of unknown supporters are responsible
for the onslaught on Spamhaus.
In an
interview with RT television CyberBunker spokesman Sven Olaf Kamphuis said
that Spamhaus has angered ISP and carrier providers for years by using mafia
tactics and blackmail to make providers disconnect clients without a court
order. He said Spamhaus wants to control all of the platforms through which
information passes.
Kamphuis
said if Spamhaus wishes to continue to exist they need to stop blocking
entire subnets and ISPs by incorrectly listing IP addresses belonging to
people who Spamhaus arbitrarily determines to be criminals, just because
they say so.
In a Skypechat
where people unhappy about Spamhaus’ actions began to organize it became
clear that many of Spamhaus’ targets are in Russia and China and that for
some reason Spamhaus lists an inordinate number of Russian and Chinese “criminals”
and “spammers” as subjects for blocking.
Kamphius
told RT that Spamhaus maintains an illegal list “without permission from
the Information Commissioners Office and in contradiction to the data protection
act, of all personal details and pictures and names and addresses of people
that Spamhaus do not like.” He also said they believe Russia and China should
not be allowed to access the internet and implied that this the motivation
for their actions and their activities are aimed with that end in mind.
Meanwhile
on Thursday there were reports that on-line banking services were beginning
to suffer, streaming media sites such as Netfix are being adversely affected
and the Guardian reports that thousands of Britons are unsuspecting participants
of the attacks as their router s have been subverted, although this last
claim is highly dubious as there is no evidence that personal routers can
be or have been “subverted” in order to carry out attacks by unknown individuals.
Several
media outlets have questioned the entire affair as a PR event for companies
which provide internet security and other such services such CloudFlare
which has sought to generate publicity for itself by becoming involved in
the attack although in reality they are incapable of dealing with such a
massive onslaught.
What we
see in the whole bloody affair is once again a trampling of freedom of speech
and expression by an organization abusing their mandate, another egregious
demonizing of Russia and China, profiteering in the name of security and
fear mongering to continue to allow for the restriction of your freedom.
As a regulator, which is the role Spamhaus has abrogated for itself, they
should be beyond reproach and operate fairly and in keeping with the law.
When they and others who purport to be in a position to dictate to the world
how to behave prove they themselves are in need of oversight and can not
follow the rule of law, they and those like them must be reigned in and
shut down and their arbitrary trampling on the rights and freedoms of others
must be stopped immediately.
There
are those in power who are afraid of information being free, in essence
information that allows the world to bear witness to their nefarious activities,
and these “individuals” will do anything to stop or control the flow of
information, whether they use mafia tactics, threats of drone attack as
NATO has done, or illegal indefinite detention as the US has done, these
individuals must continue to be exposed, if the internet is to be the vehicle
for that exposure, so be it. We as citizens of the world must be ever vigilant
of anyone trying to restrict of control our freedom and right to be informed,
under whatever guise they might be posing.
![]()
![]()
![]() Ugly Gorilla and Chinese Unit 61398 to replace Osama's Al-Qaeda as the new
global threat, or “How do we sell our overpriced product?”
Ugly Gorilla and Chinese Unit 61398 to replace Osama's Al-Qaeda as the new
global threat, or “How do we sell our overpriced product?”
20 February,
2013
11:46

A company
selling network security services has issued an extremely detailed report
on how the Chinese Army is relentlessly attacking Western computer networks
and companies. With the war on terror not really producing enough terrorists
to justify the hyper security state of America, they need a new focus to
justify cracking down on the last bit of freedom Americans have, namely
the Internet. The threat to the world is now from the Chinese Army and the
evil hacker UglyGorilla, and they will get you. Really! Run for the hills!
When a
message is being delivered by a messenger whose self interests are served
by the message, one must always be wary.
A cyber security firm
named Mandiant, based in Alexandria, Virginia,
26 minutes from the unincorporated community of Langley (the metonym for
the CIA) in McLean, Virginia, has come out with a much publicized and self-serving
report detailing the evil and dangerous threat posed by relentless Chinese
hackers.
The report
claims that advanced threat “actors”, or the more ominous sounding “Advanced
Persistent Threat” (APT), operating in China and with the blessing of the
Chinese Government, have been conducting, quote: “… a cyber espionage campaign
against a wide range of victims since 2006” unquote.
The experts
at Mandiant have no doubt done a huge amount of hacking themselves because
they have, according to their own claims, “discovered” a mountain of information
about that these evil Chinese “hackers” who are a part of the 2nd Bureau
of the People’s Liberation Army, General Staff Department Unit 61398. Mandiant
claims their information is from “open source observations” yet they make
many claims that, if they are true, point to a concentrated attack on a
very well defined location and the accessing of information that for China
would be considered secret.
The hackers at Mandiant, or as the West would call
them “cybersecurity personnel”, (U.K. Guardian calls
Western hackers who attack China “cybersecurity forces”), have apparently
discovered that Unit 61398 is involved in work that for China is a “state
secret” and that they are involved in “harmful Computer Network Operations”.
The spying
that the hackers at Mandiant have done on China does not stop there, they
have named the exact building where Unit 61398 is apparently located, its
physical address, the layout of the compound and the buildings, its square
footage, when it was built, how many people work there, the kind of wiring
and infrastructure at the facility, the training requirements of the personnel,
how many networks they use, the exact data they have “stolen”, the tools
the Chinese supposedly use, the exact length of time they have accessed
a “victims” network (example 1,764 days), the number of victims, exactly
how many terabytes of data were stolen and even three individuals who are
guilty of “following orders”.
Mandiant’s
hacking is superb, (Oh I am sorry when they do it, it is called “cyber security”),
and they even give names to these evil Chinese “hackers”: UglyGorilla, DOTA
and SuperHard! (Very Chinese sounding names of course) They even claim to
have: “… videos showing actual attacker sessions and their intrusion activities”!
They state this on page 5 of their report, right above a paragraph detailing
their “security” products and which ones you can buy.
On page
6 Mandiant does say they are: quite possibly, perhaps a little, maybe a
wee bit: mistaken, and the operations may be taking place not in the headquarters
of Unit 61398 itself but quote: “… right outside of Unit 61398’s gates.”
The rest
of the 74 page report gives details about the structure of the Communist
Party of China and includes many pages detailing how the information was
obtained, what the threats are and how you can purchase their products.
According
to Mandiant’s website the threat is dire and the only one who can save you
is Mandiant. Their site says, quote: “Mandiant is the ONLY information security
company that can both: A) TELL A COMPANY WHEN IT HAS BEEN COMPROMISED AND
B) TELL WHAT THE MATERIAL IMPACT OF THE BREECH WAS!!!
They call
this an “extraordinary statement” but personally I would go with a company
that could STOP THE THREAT BEFORE IT HAPPENED! Not tell me about it afterwards.
Mandiant
is in the business of selling threats, (well okay in the business of responding
to attacks), so the entire report may only be a self-serving marketing gimmick
and it would seem China is the great (APT). This assessment can only be
further backed up by their own gratuitous plugging of their products and
the exaggerated language present on their site.
Some examples:
“makes us the go-to company for organizations that are looking to protect
their most valuable assets”, “advanced persistent threat (APT) and other
targeted attackers that are attempting to compromise your most valuable
assets”, “known nefarious domains to perform malicious activity”, “persistent
attackers execute a series of activities to entrench themselves and compromise
your systems. If you manage to kick them out, rest assured they will be
back”, “Skilled, determined attackers can break, enter and succeed within
minutes. Other times, they spend days plotting, establishing backdoors and
fortifying their positions inside your company” and “There is no such thing
as perfect security. Attackers get smarter and change tactics all of the
time.” But with all this they will help you, for a price of course.
According to SC
Magazine “Mandiant Intelligent Response”,
the only thing to protect you from the Chinese super hackers will only cost
you a mere $86,000.00. Yes that’s right ONLY $86,000.00. (Mandiant was too
modest to post pricing anywhere on their site hence SC’s price quote and
no other prices were found).
The Guardian seems
to agree and so does Obama, the threat is real and you are a target and
China is everywhere, just like Al-Qaeda: behind every tree.
$86,000.00.
No problem. OR if you only have $80,000 and can’t seem to find that other
$6,000 measly bucks, I will give you John’s security advice for free, two
simple and cheap things any organization handling sensitive information
knows: NEVER connect a sensitive and/or secure network to the Internet and
ALWAYS hire people you know you can trust.
As for
China, I think they might have grounds to file a complaint as it seems that
they have been hacked. Or then again, maybe Obama needs to target UglyGorilla
with a drone.
Imminent
threats! Evil plots and relentless Communist attack! That is what has made
(Langley) Virginia great and the profiteers rich! Is that UglyGorrila in
your server?
![]()
![]()
![]() Orwellian methods cyber control: DDoS, Greensboro sit-ins, Anonymous comment
Orwellian methods cyber control: DDoS, Greensboro sit-ins, Anonymous comment
13 January, 2013 19:42
When there is tyranny free people must fight back,
when the tyrants try to take away that right, they must be removed. The
United States of America is attempting to implement and exercise tyranny
on the world-wide-web, this is evidenced by unproportionate fines and prison
sentences for anything they deem they do not like. Cyber space should be
free space not a prison planet. Anonymous
commented on DDoS and the Greensboro sit-ins to the Voice of Russia.
The recent
petition by supporters of Anonymous to the Obama Administration to decriminalize
DDoS attacks has now received 3,649 signatures, as of time of writing.
One of
my sources in Anonymous contacted me with some interesting facts that show
the ridiculous over kill possessed by the US authorities. If you are not
convinced that ten year felony sentences for a temporary slowdown of a location
in cyber-space which then remains undamaged is over-kill perhaps these facts
will change your mind.
According
to my anonymous source: “The severity of the sentences the government seeks
for those who have participated in denial of service protests are dangerously
out of line with the harm caused.”
The source says that according
to the US’ own data rapists serve
on average 65 months in prison, yet the government seeks sentences of ten
years, 120 months, for the nonviolent act of participating in a denial
of serviceprotest. Liking DDoS in the
virtual world to denial of service in the real world is an astute argument
but in reality the virtual kind is so much less tangible and in reality
does not even exist in the real world that it should not even need to be
compared, let alone prosecuted.
One might
argue if the people do not have the right to protest and freely express
themselves in cyber space, then the government which is supposed to be of
the people has absolutely no business attempting to regulate it or control
it.
Attempting
to control the masses and information with such Orwellian methods and such
an iron-hand is nothing if not complete and total tyranny on the part of
the US Government and the out of control police state.
The source goes on to say: “Denial of service actions
have been instrumental in the pursuit and protection of civil rights in
America. Recall that the touchstone moment of the 1960s Civil Rights Movement
was the Greensboro
sit-in where isolated and vulnerable
blacks occupied the "whites-only" lunch counter at Woolworth's.The protest
spanned days, rather than the hours typical of a DDoS protest, and the Woolworth's
lunch business was blocked entirely, while sales dropped by more than a
third. Yet for all of this disruption, protesters were largely unmolested
by the police. In fact, the police even protected a protester by arresting
an angry assailant! Ultimately, Woolworth's changed their policy of segregation
to end the protest, allowing blacks and whites to enjoy equal treatment.”
Comparing
the Civil Rights Movement to cyber sit-ins may be a little bit of a stretch
but the question here is the methodology to bring about peaceful change.
Again to contrast, the Greensboro sit-ins required dozens if not hundreds
of people putting their lives on the line and risking real world blowback.
So logically the penalty should be more severe than doing something in cyber
space. Again DDoS attacks do not damage and just slow things down for a
while. So why is the US so heavy-handed on cyber activists?
Our source
says: “Yet in recent times, the story does not end so happily. When Paypal,
Visa, and Mastercard blocked and confiscated donations intended for
protesters flooded the companies' sites to demand thatreceive the same service
that all other customers enjoy. So much internet traffic was generated by
protesters that, effectively, all of the seats at the lunch counters of
these financial companies were occupied, temporarily closing their websites.
Within hours rather than weeks, the protesters dispersed peacefully and
normal operations resumed for Paypal, Visa, and Mastercard.”
The US
government is desperate to control the internet and terrify anyone who attempts
to exercise any sort of freedom on it, just like they attempt to stifle
the freedom of speech in the real world, for several reasons. The main reason
being their own criminal conduct and the fact that the internet has done
more to show the evil and illegality of government and corrupt officials
than anything else in the history of mankind, another secondary but nonetheless
important reason is the financial motivations of the corporations which
not control the Fascist States of America.
The source said: “Today's powerful federal police,
however, no longer exercise the restraint shown by the local police of 1960s.
In the following two months, the FBI
served more than 40 warrants and
released the famous press statement calling for 10-year felony sentences
for all involved.”
In reality
DDoS attacks are a temporary headache and when addressing legitimate complaints
they should not be prosecuted at all. Prosecuting personal or damaging material,
launching personal cyber attacks or cracking into systems and defacing or
stealing information is another topic entirely. For the out of control police
state however prosecuting DDoS attacks in such a heavy handed way is just
another way to make the for-profit-prison-system more profitable, terrorize
anyone with a dissenting view into silence and protect the government’s
corporate controllers.
Source
finished with the following statement: “Anonymous stands by the example
of the brave men and women of Greensboro. History shows that the bravery
of protesters results in a more just society for all, and the public interest
is not served by 10-year sentences for peaceful resistance.”
![]()
![]()
![]()
![]() Every move you make, we’ll be watching you - US Hyper Security REX84
State
Every move you make, we’ll be watching you - US Hyper Security REX84
State
15 January, 21:27
30,000
drones flying over the United States in the next 20 years is just one of
the things Americans have to look forward too as their government continues
to turn their country into a 100% total security state. Americans have long
ago traded their “freedom” for security, so drones over Kansas should be
no real big deal. The US Government and even the local sheriff are counting
on your support, and support you will because you have no choice.
According
to the US Federal Aviation Administration (FAA) within 20 years there will
be approximately 30,000 drones flying over the United States. This month
alone the FAA approved the usage of another 348 drones to be used within
the United States.
The latest
drone-hungry law enforcement body in the US to publically declare they will
be using drones is the Sherriff’s Department of Orange County Florida, which
has stated it intends to use 2 drones this summer over the metropolitan
Orlando area. LINK 1
Proponents
of drone usage are attempting to justify yet another intrusion into the
privacy of Americans and another tool that will strip away personal freedom
and assist in creating a 100% secure-total-control-hyper-security state,
by saying they will be used to catch illegal immigrants, criminals, and
you guessed it terrorists.
The problem
here is that most Americans are buying into these false flag hyped-up arguments
based on media-spin and false propaganda being spread by their own government.
Saying
that some poor Mexican (or other illegal) who picks their tomatoes, lives
in a room with seven other illegals during the picking season only to be
deported before he can be paid when the farmer who hired him turns him in
to the Immigration and Naturalization Service because, lo’ and behold, unbeknownst
to him they were illegal, is a threat to America’s national security, is
the most disingenuous xenophobic argument one can possibly imagine.
People
conveniently forget that illegal-immigrants are exploited to no end in the
United States and then blamed for every problem under the sun. They also
forget that without them the price for most fruits and vegetables, for example,
would sky-rocket beyond affordability if union-wage paid hands were sent
out to the fields to pick the harvests. But of course for the US Government
it is easy to blame marginalized and vulnerable members of the population
for any problem they wish.
As for
criminals, the US for-profit-prison-system is holding more prisoners than
other country on earth and the US also has a larger percentage of the population
in prison than any other country on the planet.
Does a
country that can put a person in prison for life for stealing a Mars bar
on three occasions (California’s 3 strikes law) really need to be able to
spy on anyone anytime they want? And that is assuming the drones will be
used for surveillance. The next step will be arming them, again in the name
of security to facilitate arrests and stop criminals.
Does the
US law enforcement establishment need to be this militarized? The answer
is no. Do they wish to be? The answer is they absolutely and without a do.
What about
the terrorist claim? Well, to be frank the entire US terrorist threat is
pure hype. Unless of course we take into account the self-created terrorist
threat that has existed since 9-11. However even after more than a decade
of slaughtering supposed “terrorists” their families and everyone around
them, perhaps in the hope of creating real terrorists and thousands who
will seek revenge for the killing of their families, there has yet to be
a real terrorist attack in the United States of America.
So there
you go American populace, you have been duped and the real planners of 9-11
have been rolling over and laughing at you since day one. Here you were
asked to believe that some ex-CIA agent (Osama bin-Laden a.k.a. Tom Ossman)
organized the most precision demolition in the history of mankind and staged
it to look like a terrorist attack using pilotless “drone” aircraft from
a cave in Afghanistan, and you believed it. Then you were asked to believe
that behind every tree and lamp-post there lurked an al-Qaeda terrorist
from the local “cell” that exists in every “hometown” American city, and
you believed that too.
So they
stripped you of one right after the other and you agreed because you felt
afraid and terrorized and trusted your government, yet who in fact was terrorizing
you? Your own government and your government-and-corporate-controlled-mass-media,
who have worked hand in hand in creating the corporate-controlled fascist
state you live in today.
So Americans,
you have video cameras on every corner, you have bar codes and computers
that record your purchases and upload them to your “file” when you use your
credit card, you have dentists who record and upload your data to central
data-bases, you have AGPS devices with internet connect-ability that record
your every move and can now even determine what floor you are on, cell phones
that can be used remotely to listen and even watch you through the camera
and which can track your every move, you have traffic cams that record your
license number and can ticket you by mail, laser radar that can record your
speed from three miles out, auto-mounted transmitters that can help track
your vehicle no matter where you might be, satellite cams that can read
the title of that paperback you are reading while you try to fall asleep,
cameras that can see through walls, acoustic, microwave and other weapons
that can cook you alive from the inside from a distance, data-bases of your
every move from a doctor’s visit to a late electrical bill, facial identification
software being used in public places, retinal scans, brain scanning devices
that can supposedly pick up the “abnormal” brain activity of a terrorist,
and that is not all. They want to put RFID chips under your skin with all
of your information stored on them that can be activated remotely, they
already have RFID chips used to track consumer goods and cars and even students
(Texas), warrantless wire tapping and surveillance to listen to every word
you say and to watch you whenever they want, you have data bases that record
all your activities on the internet and Carnivore which saves and records
every e-mail and fax you send, there are even tiny micro-chips in your money
which record every bank where that money has been, and then there are the
lists: the black lists, no-fly lists, watch lists, secret police lists which
might contain such information as the fact that you keep a shot gun under
the bed in the right corner, etc. etc., so with all that America what is
a drone?
If you
were to enter the “secret” DHS or CIA or NSA rooms where there are huge
screens that they use to track and record everything and anything they want
and can bring you up with a few key-strokes and see where you are and what
you have been up to, including what you had for dinner last night, you would
understand that you are no longer free.
I personally
don’t feel too bad for Americans, they have blindly allowed all of this
to come about and unfortunately for them it is too late.
Meanwhile,
is Russia we have traffic cams, registration stamps with our addresses,
and very competent security services who actually prevent real terrorists
from attacking. Without demanding the enslavement of the people.
The public interest is not, but the corporate and police state’s interests are. If the people no longer have the right to protest, then they are slaves of the system, and that is exactly what those in power in America want.
![]()
![]()
![]() Remember that MP3? The police are en-route
Remember that MP3? The police are en-route
10 December
2012, 19:30 1
With
the US ready to send Anonymous Hacktivist Jeremy Hammond to prison for life,
Jullian Assange stuck in limbo in an embassy, Commander X and Anonymous
members being hunted, is the world about to allow the US and its surrogates
to come after all of us? Apparently it is. The total enslavement of mankind
will soon be here, brought to you by the fascist United Corporate States
of America. Recently the International Telecommunications Union (ITU) met
in secret to decide on new ways to control the World Wide Web.
In a
very quiet release of information the Internet Warriors and “Hacktivist”
Group Anonymous, has informed the world of one of the tools that will be
used to bring this about. If you have ever downloaded a song for example,
or transferred it to your cute little harmless looking MP3 player, or listened
to it off a USB flash drive in your car, or copied it to another computer,
or God forbid, shared it with a friend, this applies to you. You are a criminal,
you have violated US law and they will come after you.
The ITU
was originally known as the International Telegraph Union a United Nations
agency responsible for controlling information and communication technologies.
The ITU’s activities include global coordination of the use of the radio
spectrum, cooperation in determining satellite orbits, telecommunication
infrastructure development in the developing world, and assistance to countries
in the development and coordination of worldwide technical standards.
Their
sphere of influence includes the entire planet and every user of the World
Wide Web is affected by their decisions, so it is alarming that they would
meet in secret and that the contents of their work would only be made public
via an Anonymous “secret document” release.
The technology
that was approved and discussed at the conference and has internet freedom
proponents up in arms is called the Deep Packet Inspection Standard (DPI),
it is a crucially important technology for the mass world-wide surveillance
of the internet.
Some
immediate uses of the DPI, according to the ITU and Anonymous include:
technology for tracking and identifying the users and sources of the BitTorrent
system (used for transferring films, programs, music and almost anything
else electronic), identifying and tracking copyrighted material (including
music, video, electronic books, photographs, etc.), identifying the exact
content and nature of transferred files and their source, blocking and controlling
Session Initiation Protocol (SIP) messages used in video and audio communications
uplinks, measuring and eventually controlling Jabber traffic (In Spanish
for some reason. Jabber was originally called Extensible Messaging and Presence
Protocol (XMPP) this is communications protocol for message-oriented software
based on XML Extensible Markup Language used extensively by social networks
VoIP communications and gaming traffic) and finally identifying source and
controlling VoIP itself (VoIP stands for Voice over Internet Protocol),
used in such things as voice communications and SMS communications over
the internet.
Without
getting too technical, in brief this will make almost anything and everything
you do over the internet subject to even easier inspection and monitoring
and in the end prosecution by, (Who else?) the US and its surrogates.
According
to several hackers on Anonymous forums, the DPI will effectively make it
easier to monitor, prohibit, identify and control the net, and as one individual
put it “These standards would lower the learning curve for the NOC (NOC
stands for Network Operations Center, a location where a network is monitored
and controlled) monkeys considerably,” meaning their knowledge of scripts
and networking technology and other tools will have to be much less.
We know
that the World Wide Web was first developed to hide a global
military network which
still exists today and that one reason Bill Gates became so rich was that
his “Windows” platform, with its secret source code, contained secret backdoors
for the government which allows the spying on any computer connected to
the internet, so now this will be taken to the next level and allow for
them to openly go after anyone they see fit.
With
the role of the US as the world’s policeman expanded so it is now an out
of control super-power unilaterally engaged in extra-judicial executions,
launching invasions at will and a million other practices that subjugate
and enslave the world, the day will soon come when: if a user in Bora-Bora
downloads an MP3, he may get a knock on the door, or perhaps he will be
fined on the spot and his bank account will be hit for the cost of the “violation”.
If you
say, “Hey, all my software is legal, so what?” you will need to worry about
everyone you come into contact with. What if someone sends you an “illegal”
attachment? You will be liable. What if someone you are talking to on Skype
mentions the words “president” and “bomb” in the same conversation? You
will be under surveillance. No matter where you are or who you happen to
be.
One telling
aspect of the ITU’s meeting was the list of who was not allowed to attend, according
to RT such
“deviant” organizations as Google, Facebook and Twitter, and what was not
allowed to be discussed; namely proposals from countries the world over
who will be affected by yet another unilateral US decision.
Apparently
is it not enough for the US Government that Facebook was forced to provide
the CIA with its own special interface, they want more, they want complete
and total control of the entire pie.
In this
day and age of continual aggressive invasions and the continued distribution
and attempted distribution of false information to facilitate support for
such heinous acts, the internet is the last resort for many the world over
to learn the truth about what is really happening. For Americans, apart
from foreign media, the internet is the only place where they can actually
learn what is really happening.
A government
that is afraid of information being shared is a government that is engaged
in evil. They need to control you, because they are afraid of you, they
need to shut you down because they are afraid of what you might learn, that
what they are doing is illegal and that they are engaged in crimes against
all humanity.
Imagine
a day when you attach a retinal scanner to your eye, and a device reads
the chip implanted in your skull before you log onto your computer, to write
a letter to your mother that may be rejected by Carnivore and the NSA because
you accidently wrote bomb and president in the same sentence. Imagine you
are then locked to your seat, by hidden steel restraints that immobilize
you so the authorities can come and take you away. Or imagine you are sent
a song and begin to listen only to have a warning pop up on the screen advising
you to stay where you are the copyright police are on the way, sound fantastic?
Not really just the next logical step.
Rather
than using encryption and other technologies to make file sharing impossible
they want to criminalize it, and more importantly, criminalize you, then
they will have the “right” to take away your freedom and whatever else you
have that they desire.
![]()
![]()
![]() US Adm Wants Total Control in Cyberspace
US Adm Wants Total Control in Cyberspace
15 September 2012, 12:26
The recent upheavals in the world
have taken attention away from a very important move by US President Obama
that could strip away another large chunk of freedom from Americans and
place another huge and important piece of the public domain under government
and corporate control. President Obama has circulated an executive order
that will implement measures that have already failed to pass Congress and
were contained in the failed Cybersecurity Act of 2012. Again the pretense
for stripping away freedoms is “security” and again the attackers are China
and Russia.
Whenever
the US issues another order or law regarding “security” the hairs on the
back of my neck stand on end. Why? Because this means that even more rights
and civil liberties will be stripped away from the people and even more
power will be had by the government.
Reports
say that the Obama Administration is currently drafting what is called in
the US, an executive order, giving the Department of Homeland Security (DHS)
the power and the responsibility to establish standards of cybersecurity
that would protect banks, water plants, telecommunication networks and the
U.S. power grid from electronic attacks.
On the
surface and to those who know little about the real cyber attacks, the program
dubbed Perfect Citizen, looks like something that is needed and should have
been implemented yesterday, but hold on a minute, the devil is in the details
and in who is behind the plans, namely the most secret of the secret US
Security structures, the National Security Agency or NSA.
The problem
with that for US citizens and in general is that it would give an intelligence
agency control over a public system which may be an area of expertise by
the NSA, responsible for signals and electronic security, but goes against
the NSA directive not to spy on US citizens.
The plan
which has wide-ranging implications and will basically allow the government
to take control over the electronic grid, and this includes the internet,
is deemed necessary by its proponents because the power grid of the United
States is supposedly vulnerable and under constant cyber-attack. However
this is far from the truth.
According
to Michael Tanji over at Wired,
first of all the networks in question, power grids and the public water
supply systems are rarely if ever connected to wide area networks and the
public internet. Secondly the operating and control systems they use are
often proprietary, meaning they have no publically or even privately available
analogues that are available and accessible to the public or to hackers
who can reverse engineer them and find weaknesses or vulnerabilities that
they can exploit.
So the
law is not needed and the rationale behind it is false then why attempt
to pass the law, bypassing the legislative branch, by using an executive
order to do so? First of all because a similar bill failed to be passed
into law earlier this year and second of all for the reason I have already
stated, it would allow the US Government to take control of the internet
and the public electronic grid which includes almost all forms of modern
communications.
According
to propaganda put out by the continuously more powerful Department of Homeland
Security there are constant attacks that target everything from the US power
grid to nuclear power plants.
Even
scarier is information being disseminated by the National Security Agency
itself. A report published byReuters quotes
the head of NSA's Information Assurance Directorate, Debora Plunkett when
asked how real the threat of hacking from China, Russia and other countries
was, as saying: "Significant. I don't know how else to describe it."
Even
worse she said that: "Some of today's national cyber actors don't seem to
be bound by any sense of restraint." Meaning state sponsored cyber-attacks
are out of control and state actors behave recklessly.
Again
the White House is demonizing China and Russia which they claim are attempting
to commit computer espionage in a wide range of areas and for wide ranging
reasons. This and other false propaganda about massive attacks on critical
infrastructure is designed to terrify the American populace into giving
away even more of their freedoms and rights, yet despite this the Cybersecurity
Act of 2012 failed and there are not public cries begging for more “protection”.
According
to the US media the Obama executive order bears a striking resemblance to
the Cybersecurity Act of 2012 which failed to be passed by Congress. Many
also say that an executive order in this instance violates Article 1, Section
1 of the US Constitution which says: “All legislative Powers herein granted
shall be vested in a Congress of the United States, which shall consist
of a Senate and House of Representatives.” Nowhere in the US Constitution
does it say that if a bill is not passed the president can single-handedly
decide to make a law himself.
The practice
of using executive orders is a controversial one which many see as a tool
of an “Imperial President” as they allow the president to unilaterally and
without oversight or public debate pass laws that may not be in the public
interest. Former US President George Bush was famous for issues such orders
many making crimes such as torture illegal after the fact and other designed
to protect him and his administration from bothersome oversight, such as
an executive order limited access to presidential papers.
The greatest
fear regarding this executive order is that a partnership between the government
and corporations under the guise of “security” to jointly control the entire
US electronic grid is a step to merging corporate and state power, a condition
which is better known as corporate fascism.
There
may be a real threat here, but the question lies, from where?
![]()
![]()
COMPUTING, HACKING AND SECURITY: Further Reading and Education
![]()
![]()
![]() Computer Networks and Information Warfare Implication for Military Operations
Computer Networks and Information Warfare Implication for Military Operations
http://www.jar2.com/Files/USGOV/csat17.pdf
![]()
![]()
![]() Anonymity/Security
Anonymity/Security
../Files/Anonymous/Anonsec.pdf
![]()
![]()
![]() US Government NSA, FBI and CIA Cyber Operations Hacks and Programs
US Government NSA, FBI and CIA Cyber Operations Hacks and Programs
../Files/USGOV/USG_Exploits.txt
![]()
![]()
![]() ANONsec: Anonymous IPsec to Defend Against Spoofing Attacks
ANONsec: Anonymous IPsec to Defend Against Spoofing Attacks
../Files/Anonymous/draft-touch-anonsec-00.pdf
![]()
![]()
![]() Multiple Browser Security in One (11 pages)
Multiple Browser Security in One (11 pages)
Files/Anonymous/appisolation.pdf
![]()
![]()
![]() The Art of Intrusion: Hacker, Intruder and Deceiver Exploits (291 pages)
The Art of Intrusion: Hacker, Intruder and Deceiver Exploits (291 pages)
www.jar2.com/Files/Leaks/Hudburgh/taoi.pdf
![]()
![]()
![]() Hacking for Dummies: Test Network Security Ethically (387 pages)
Hacking for Dummies: Test Network Security Ethically (387 pages)
http://www.jar2.com/Files/Books/Hacking_for_Dummies.pdf
![]()
![]()
![]() Pentester Lab Web Penetration Testing (106 pages)
Pentester Lab Web Penetration Testing (106 pages)
http://www.jar2.com/Files/Books/web_for_pentester.pdf
![]()
![]()
![]() Hacking Firewalls and Networks: How to Hack into Remote Computers (356 pages)
Hacking Firewalls and Networks: How to Hack into Remote Computers (356 pages)
![]()
![]()
![]() The Art of Deception Controlling the Human Element of Security (335 pages)
The Art of Deception Controlling the Human Element of Security (335 pages)
http://www.jar2.com/Files/Leaks/Hudburgh/mitnick.pdf
![]()
![]()
![]() The Hacker's Handbook By Hugo Cornwall
The Hacker's Handbook By Hugo Cornwall
http://www.jar2.com/2/Computing/Hugo%20Cornwall%20The%20Hacker's%20Handbook.htm
![]()
![]()
![]() Hacking Firewalls and Networks
Hacking Firewalls and Networks
![]()
![]()
![]() The Anon/Guccifer Files: Pisces: Anonymous Communications Over Social Networks
The Anon/Guccifer Files: Pisces: Anonymous Communications Over Social Networks
http://www.jar2.biz/Files/GUCCIFER_AND_ANON_HACKS/anonymous-sm-comms.pdf
![]()
![]()
![]() The Anon/Guccifer Files: NSA: The Next Wave - Review of Emerging Technologies
The Anon/Guccifer Files: NSA: The Next Wave - Review of Emerging Technologies
http://www.jar2.biz/Files/GUCCIFER_AND_ANON_HACKS/nsa-tnw-19-4.pdf
![]()
|
Copyright JAR2 2003-2103 All Rights Reserved Publishing Banned Truth Since June 06, 2003
|